Add encrypted signatures to webhook headers
You can ensure webhooks are secure by generating a signature to verify the source and payload. By default, Orange Logic uses HMAC SHA-256 for authentication. You can change the signature hash method used for authentication to HMAC SHA-512.
Here’s an overview of the signature verification process:
-
Orange Logic and the webhook recipient share a secret key.
-
Whenever Orange Logic sends a webhook, it takes the secret key and adds a hash algorithm to create an encrypted signature in the
x-ol-signatureheader. The output format for the signature is Base64.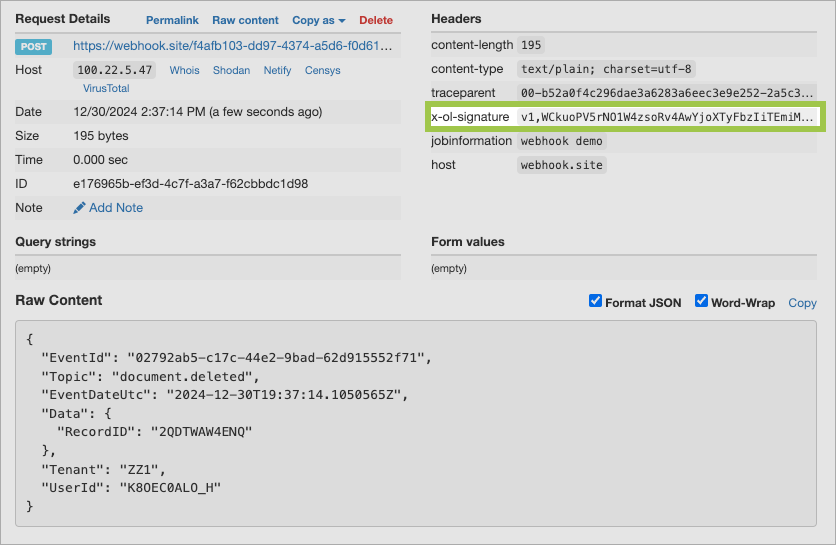
x-ol-signaturein a test webhook header. -
When the webhook arrives at the webhook URL, the recipient uses the secret key and the algorithm to calculate the signature.
-
The recipient compares the calculated signature to the one sent by Orange Logic.
-
If the signatures match, the request is valid and the recipient accepts the webhook. If the signatures do not match, the webhook is rejected.
Notes
- The ability to sign a webhook’s payload is available beginning in the Orange Logic Kobe release.
- This feature is deactivated by default. To learn how to activate this feature, go to the Activate and configure webhook signatures section.
Super Admins: Configure webhook signatures
Here are the steps to add a signature to your webhook. You must be a super admin user to complete the steps below.
- Activate webhook signatures.
- Create the webhook subscription.
- Generate the secret key with the RotateSecret API.
Activate and configure webhook signatures
Super admins can activate and configure webhook signatures in the Configure Modules Advanced Configuration.
- Go to Administration > Reference Tables > Configure Modules. The Configure Modules form opens.
- Go to the Webhooks section.
- Select the checkbox to activate webhook signatures.
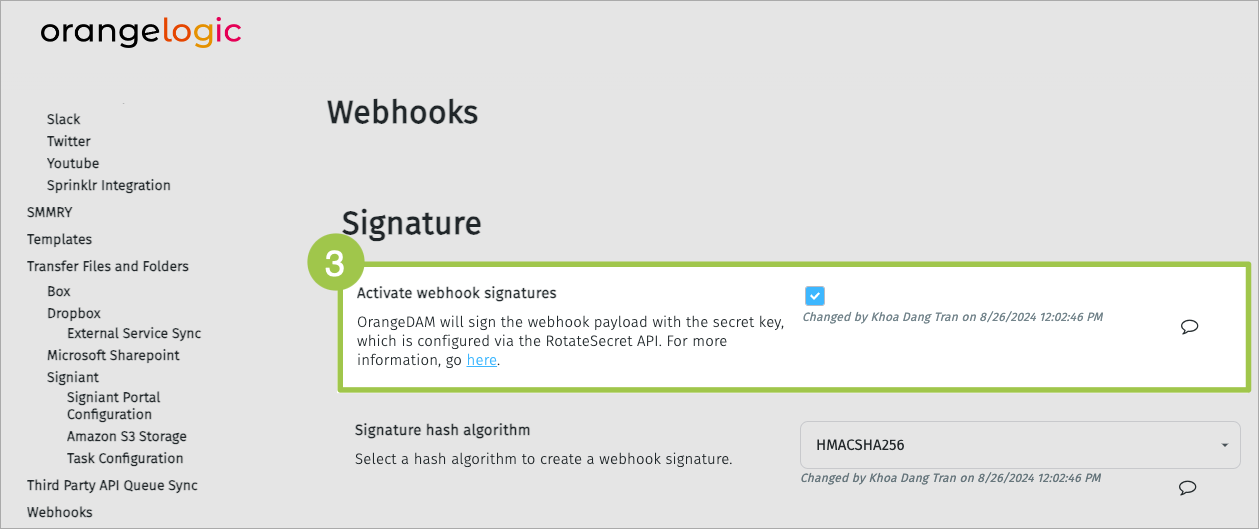
Activate webhook signatures in the “Configure Modules” form.
- (Optional) You can configure other webhook settings in this form, including the signature hash algorithm used for authentication and secret rotation time.
- Click Save.
